WordPress is an open source project and developed by the community from all over the world. A lot of expert spent their times to make WordPress as secure as possible. But I'm not in the position to say that it has bulletproof for security vulnerability. You can see there are couple security has been reported fixed and disclosed in WordPress hackerone. You can report any security issue too, if it is valid, you'll get bounty!With that said, I would like to share couple best practices I did to … Read more...

Secure Your Connection With Your Own Cheap OpenVPN
I did experience when my "naughty" ISP inject a javascript to a web page when the site is not using https. That script intended to track, and maybe steal some cookies (I'm not sure, since they can get anything). And another story also when I did use public wifi when I work in a cafe/coworking space, and I got SSL warning that there is man-in-the-middle try to intercept my connection, and said the SSL certificate is not valid. I was shocked that it is not hard for a sysadmin to intercept our … Read more...

Linux Shellshock Security Patch
Just doing a routine browsing this morning and i found that my Ubuntu is vulnerable with Shellshock attack. Shellshock is newly discovered security vulnerable for your bash, which means all Linux and Max are vulnerable from this security issue. Shellshock using crafted environment in bash script and gain access to your computer. This is more serious than heartbleed a while ago.To test if your Linux is vulnerable, run this script on your bash terminal:If you see a message: vulnerable … Read more...
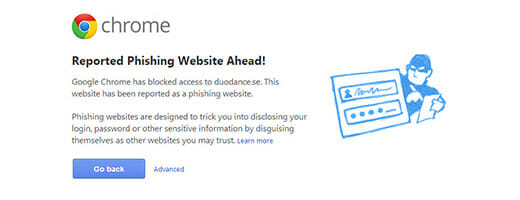
Phising Through Email Using Google Drive Link
Recently i found that some of my friends send me an email asking to see an important document in Google Drive. The title would say "Kindly Review The Uploaded Document" and here is the content of the email: Hello,please see this it's very important https://drive.google.com/ and sign in to viewIt's very importantKind regards Please see the screenshot below:The email sent to me as bcc as my contacts, so i thought it might be something important. But i'm shock when … Read more...

Have You Done GMail Security Checklist?
To know that your account is being hacked is the worst nightmare ever. Especially when you have a confidential information such as finance information in that account. Most of the internet account need email for communication. And even Google mail have the best security (in my humble opinion), could be compromised if you are not careful. Amit Agarwal from labnol got his GMail hacked once and he managed to recover it back after some time.Actually Google Mail has the security checklist in … Read more...

How Facebook Account Been Hacked
There have been many report that their Facebook account has been hacked by the anonymous. My cousin also report that his Facebook account being hacked even he use a fairly strong password and really keep his password safe. Even Amit Argawal from Labnol also has been hacked recently, read his post "My Facebook Account Got Hacked"."I no longer have access to my Facebook pages!", said Amit in his blog post. As the technology journalist i'm pretty sure that he used a strong password for all of … Read more...
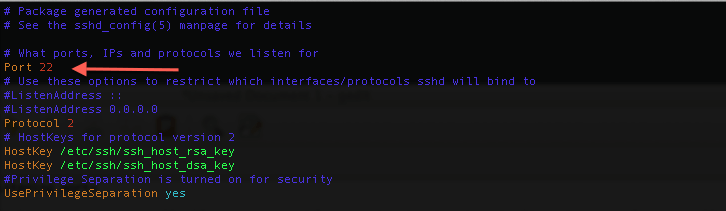
Beginners Guide: Change SSH Port On Ubuntu Or CentOS
If you install CSF (ConfigServer Security & Firewall) you will find in their recommend list that you need to change your SSH port for security reasons. And changing SSH port in both Ubuntu or CentOS is not hard.To change SSH port in Linux (Ubuntu or CentOS): 1. Open your terminal with root access 2. Edit ssh_config file:3. Change the port4. Save and close. Then restart your SSH Server:It's easy right? Now when you connect to SSH from putty probably, you need to use port … Read more...

New Google Security System: 2 Steps Verification
Google just launch a new security feature to access Google Account. It is called 2-steps verification. With this 2-steps verification, the hacker cannot enter your account only with your hijacked password. They need to enter the verification that will be sent to your mobile phone or generate the verification number using Android, Blackberry and iPhone application.I've been using this security technique for my internet banking, which will ask the 2nd verification using a Token device. So … Read more...

Disable Autorun and Autoplay In Windows 7
Windows 7 is the latest series of Microsoft Windows operating system. Some says it have better security than its predecessor. With it's bitlocker, applocker and smarter user account control (UAC) offer user better security. But it still have the same old hole, autorun and autoplay feature which offer user simplicity, could turn into double edge sword. "Attacker" use this hole to insert or run virus and trojan. And steal your personal data.So the quick tips to secure your Windows 7 is disable … Read more...

Hardening Your Server Security With ConfigServer Security & Firewall
Talking about server side security will come down to firewall or filter connections from and to your server. Close unnecessary ports, block unwanted connection and blacklist spammers are the things that your server admin should do in their everyday life. If you pay attention to your server log, you will found that lot of malicious request and brute force bot attack to find your server vulnerabilities. You should block it with firewall.One of the good and free Firewall module is ConfigServer … Read more...
